Splunk isnt on the officially support list of apps that can intergrate with G-Suite SAML, but it can be manually addded. This is the process i went through just last night to intergrate G-suite SAML with Splunk.
Adding a Custom Attribute for users in G-Suite
In the “Users” page, Click on the “Manage Custom Attributes” Button at the top:
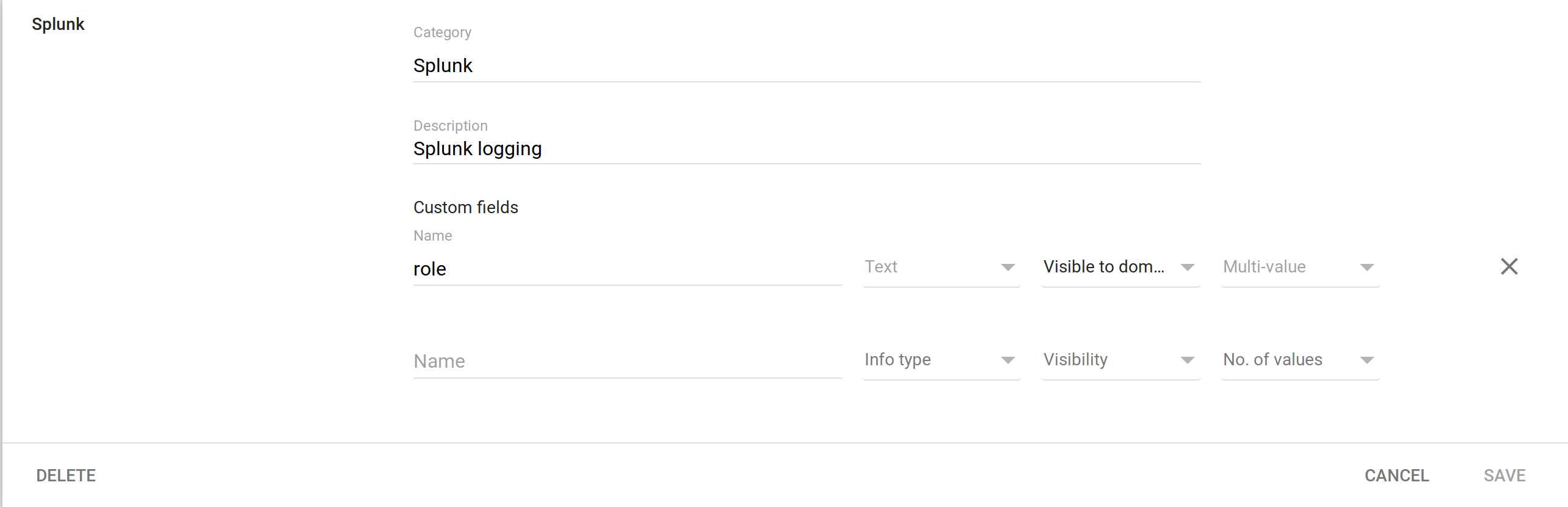 Thats all that needs to be added in the “User” Section for now.
Thats all that needs to be added in the “User” Section for now.
Adding Splunk to the SAML Apps
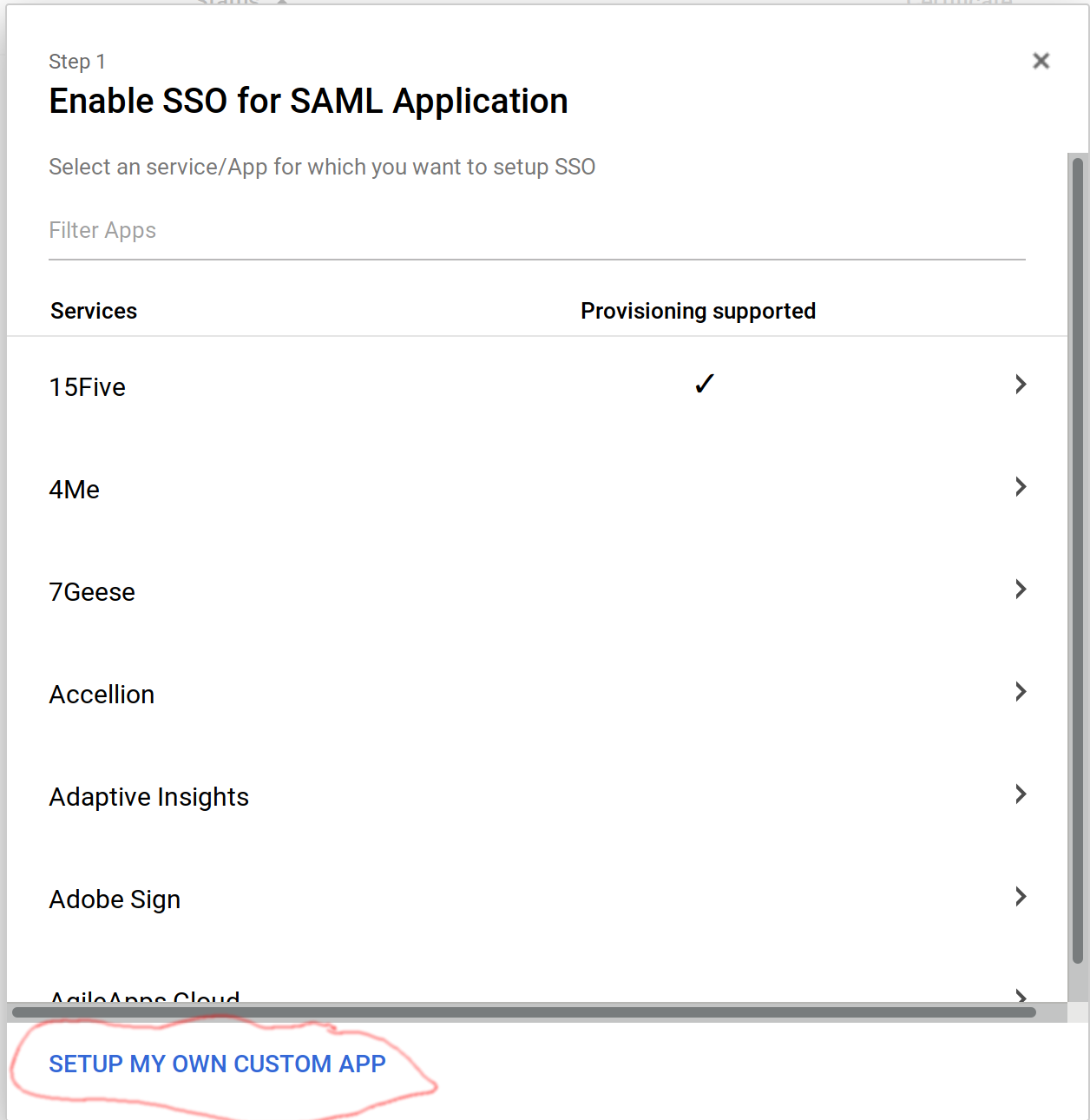
Next we need to add Splunk to the SAML Apps. As noted above, this isnt in the list of apps you can quickly setup, so you need to choose “Set up my custom App”:
 In the next screen you get the SSO URL along with the Entity ID and certificate.
In the next screen you get the SSO URL along with the Entity ID and certificate.
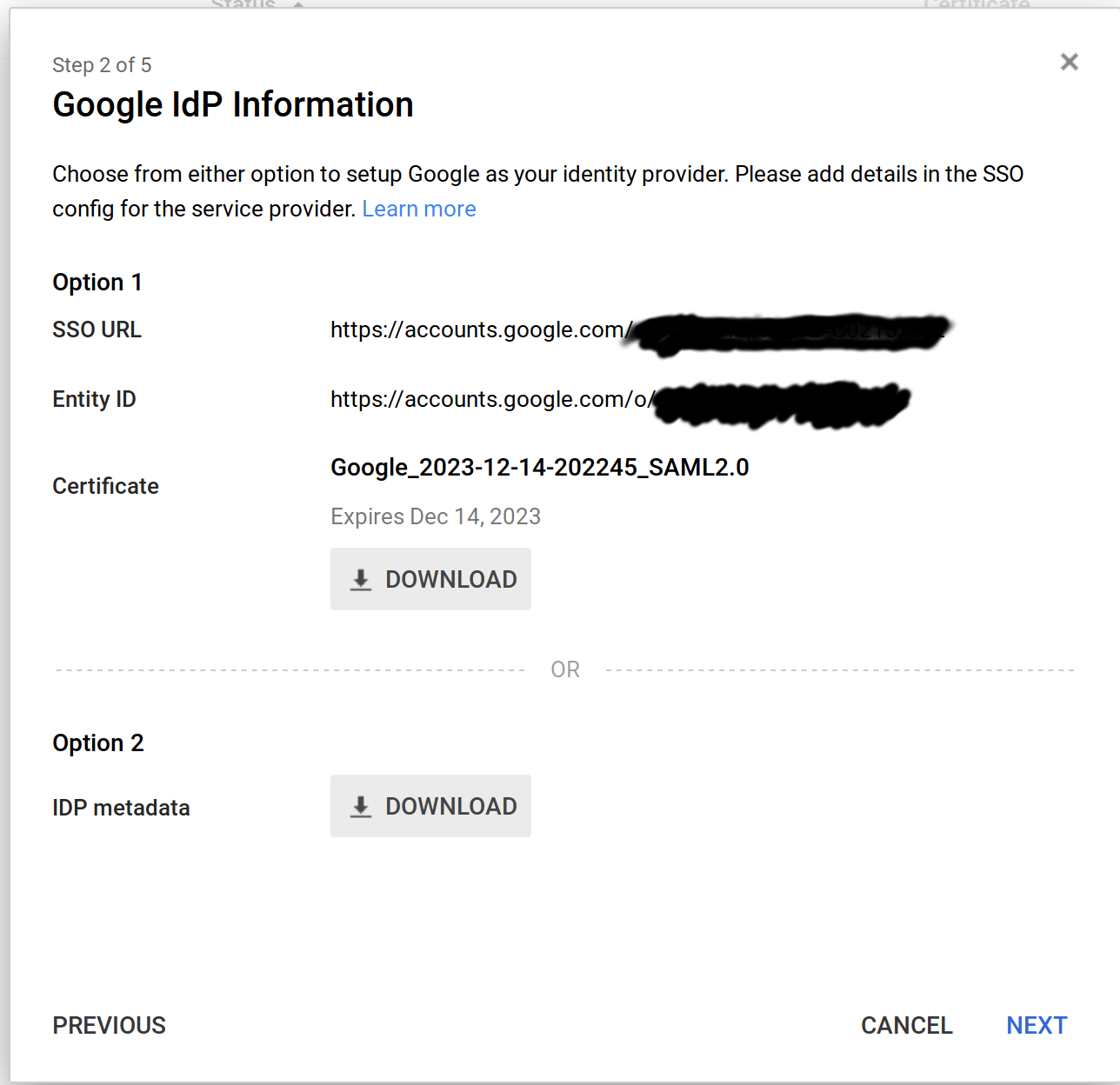 Make sure you note down the SSO URL, Entity ID and download the certificate. Press Next.
Make sure you note down the SSO URL, Entity ID and download the certificate. Press Next.
Youll now get the App Info screen, fill it out how you want:
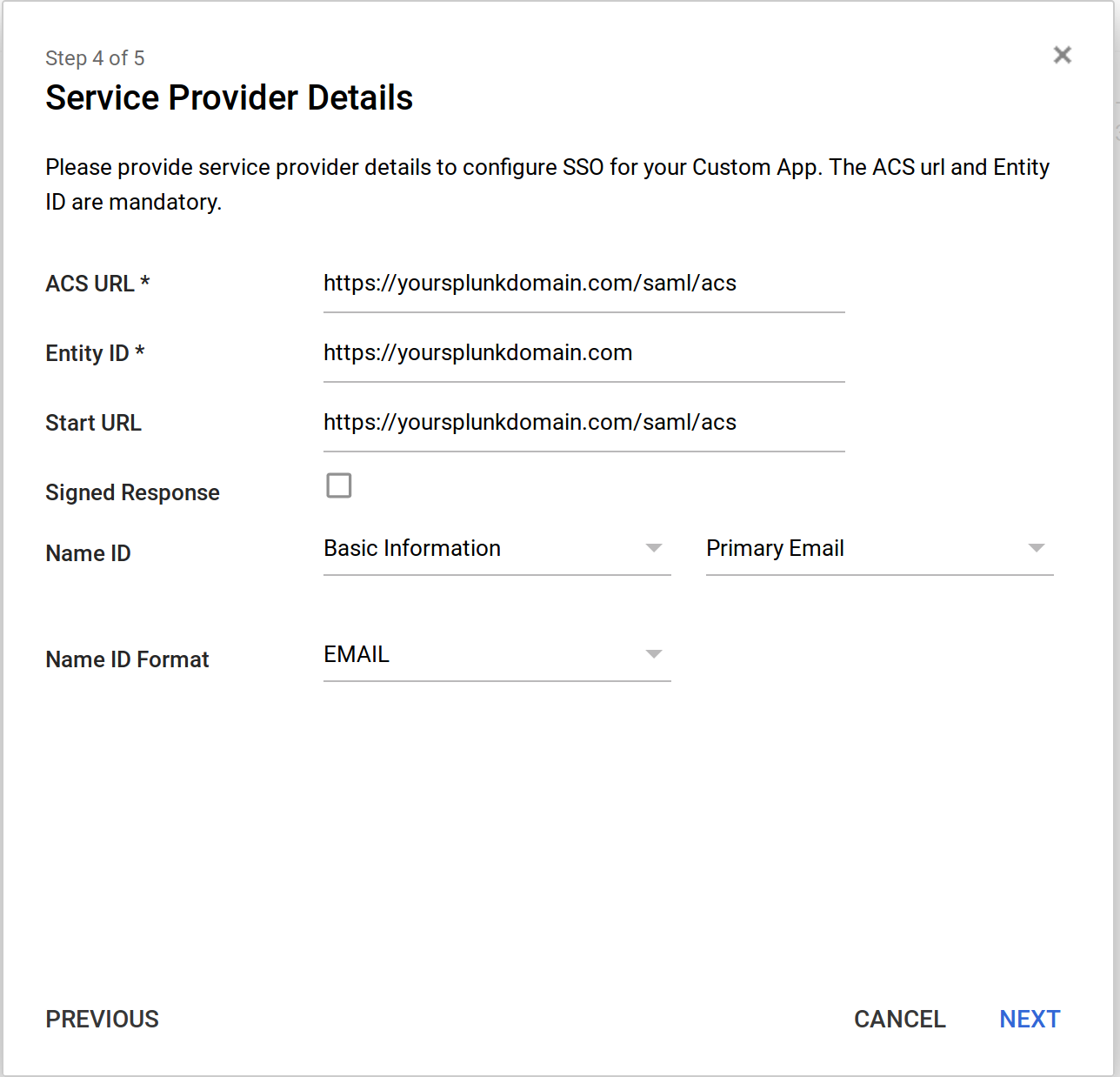
 Next is the Service Provider Details page. Use the following details:
Next is the Service Provider Details page. Use the following details:
ACS https://yoursplunkdomain.com/saml/acs
Entity ID https://yoursplunkdomain.com
Start URL https://yoursplunkdomain.com
Name ID Basic Information and then Primary Email
Name ID Format Email
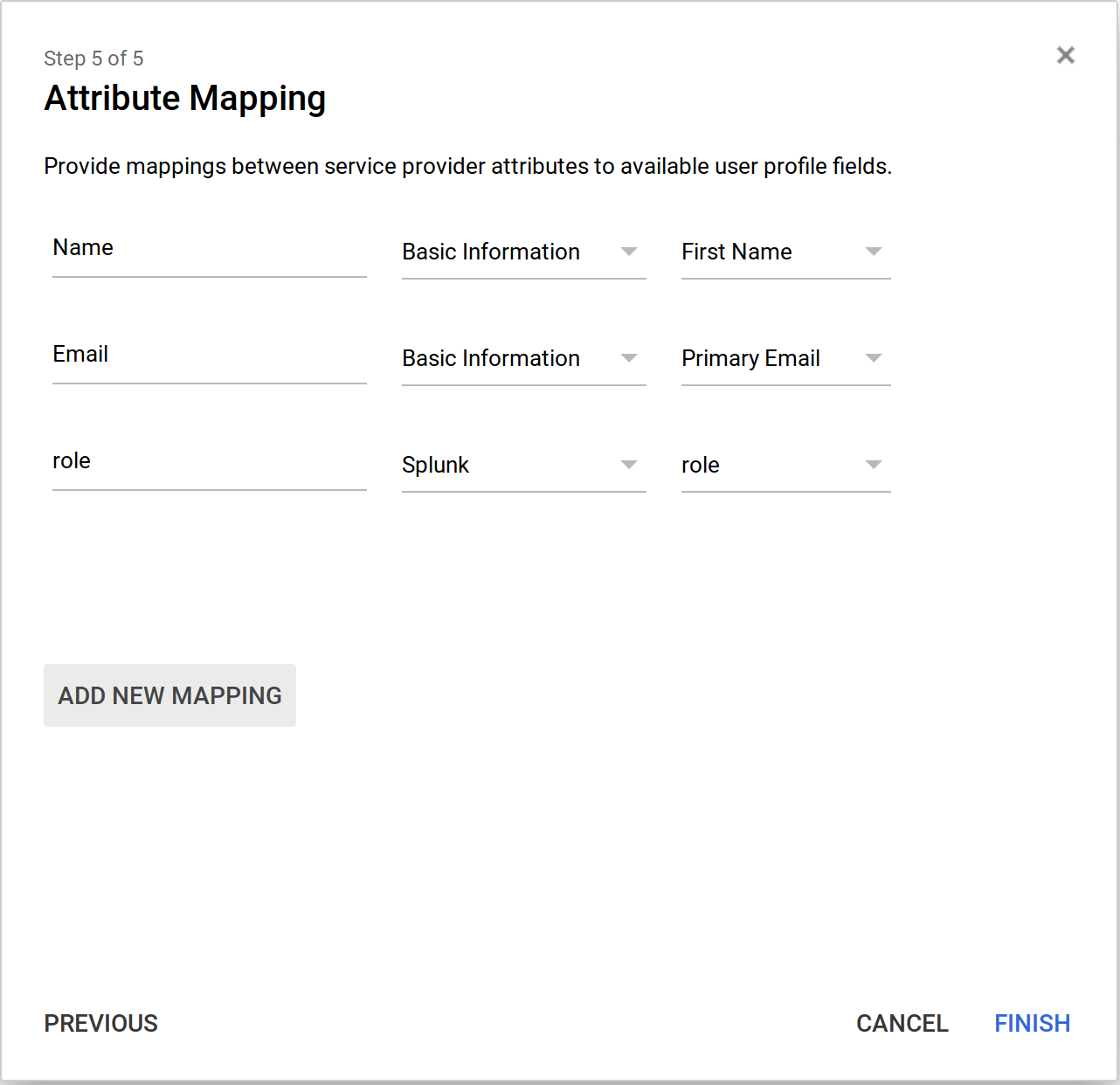
 Next is attribute mapping, you need to click “ADD NEW MAPPING”. Configure it as follows:
Next is attribute mapping, you need to click “ADD NEW MAPPING”. Configure it as follows:
Configure Splunk
Firstly, if you get locked out of your splunk instance due to misconfiguring SAML, add the following onto the end of your URL to bypass SAML /en-US/account/login?loginType=splunk
Before starting, you will need to upload the certificate you downloaded earlier. This needs to go in (on a standard install, on the search head): /opt/splunk/etc/auth/idpCerts. You might need to create that directory.
- Log into Splunk web UI
- Go to Settings Then Under “Users and Authentication” select “Access Controls”
- Click “Authentication Method”
- Select SAML under External then click SAML Settings
- Click SAML Configuration in the top right
- Now fill out the details as follows.
Single Sign On (SSO) URL – SSO URL you was given when creating the aoo on G-Suite.
SLO – Set it as “https://accounts.google.com/Logout?hl=en&continue=https://mail.google.com/mail”
IdP certificate path – If you uploaded the cert as noted above, just put the filename of the cert.
Issuer ID – The G-Suite Entity ID
Entity ID – The Entity ID you entered when creating you app.
Near the bottom, there is “SSO Binding” and “SLO Binding” Set both to “HTTP POST”.
That should be all you need to configure.
Extra configuration when splunk is behind a reverse proxy.
After completing the above configuration, was getting error stating the ACS was incorrect due to the hostname of the search head not matching. This is because i had a different hostname on the search than i did for the url accessed via the reverse proxy.
All i needed to change was the following 2 settings:
Fully qualified domain name or IP of the load balancer – https://publichostname.com
Redirect port – load balancer port – 443